MIS – adalah satu dari banyak mata kuliah yang diberikan kepada mahasiswa TeknikIndustri, Universitas Indonesia
Sesuai namanya, MIS adalah bagaimana mengelola suatu informasi dalam suatu sistem yang dapat memberikan manfaat yang sangat penting didalam bisnis.
Bicara MIS, maka tidak dapat dilepaskan dari yang namanya Computer (hardware&software)
Sejak tahun 1950-an, terjadi perkembangan yang sangat dramatis didalam penggunaaan Hardware dan software komputer baik secara individu maupun perusahaan.
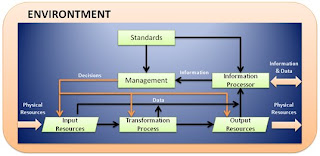
Berikut adalah model umum MIS dalam suatu perusahaan
McLeod, page 26
REVIEW MATA KULIAH
KNOWLEDGE MANAGEMENT :
Adalah sistem informasi yang dirancang untuk memfasilitasi, mengenali, mengumpulkan, meng-integrasikan dan menyebarkan knowledge dalam organisasi.
KM systems fokus dalam membuat, mengumpulkan, mengelola dan menyebarkan knowledge daripada data dan informasi
Davenport and Prusak (1998) states 8 principles of knowledge management. They summarize. what is known and are worth repeating here.
1. Knowledge originates and resides in people’s heads
2. Knowledge sharing requires trust.
3. Technology enables new knowledge behaviors
4. Knowledge sharing must be encouraged and rewarded
5. Management support and resources are essential
6. Knowledge initiatives should begin with a pilot program
7. Quantitative and qualitative measurements are needed to evaluate the initiative
8. Knowledge is creative and should be encouraged to develop in unexpected ways.
E-COMMERCE
Electronic Commerce- Penggunaan Komputer dan jaringan di dalam bisnis, dengan kata lain Jual beli produk menggunakan internet.
Ada dua jenis e-commerce, yaitu:
· Business to Cunsumer (B2C) - transaksi yg terjadi antara pebisnis dan konsumenya
· Business to Business (B2B) – transaksi yg terjadi antara dua pebisnis
BARCODE
Barcode adalah salah satu metode didalam pengumpulan dan identifikasi data secara otomatis Ditemukan dan dipatenkan senilai 2.612.994 USD pada Oktober 1952 oleh Joseph Woodland dan Bernard Silver
DEFINISI – Suatu gambar kecil yang memuat garis dan spasi sebagai kartu identitas untuk mengidentifikasi suatu produk tertentu, orang dan lokasi. Kode yang memperlihatkan batang/garis vertikal dan spasi yg mewakili simbol dan nomor tertentu
Barcode biasanya terdiri dari 5 bagian, yaitu:
1. Quite zone
2. Start character
3. Data characters
4. Stop characters
5. Another quite zone
tapi bagaimana barcode bekerja??
Scanner membaca Bar dan spasi yang ada di label. Angka hanya untuk manusia. Informasi dari scanner ditransfer ke komputer yang sudah terkodifikasi dan memuat data harga, sisa barang yg tersedia dan data lainnya
Adalah sistem informasi yang dirancang untuk memfasilitasi, mengenali, mengumpulkan, meng-integrasikan dan menyebarkan knowledge dalam organisasi.
KM systems fokus dalam membuat, mengumpulkan, mengelola dan menyebarkan knowledge daripada data dan informasi
Davenport and Prusak (1998) states 8 principles of knowledge management. They summarize. what is known and are worth repeating here.
1. Knowledge originates and resides in people’s heads
2. Knowledge sharing requires trust.
3. Technology enables new knowledge behaviors
4. Knowledge sharing must be encouraged and rewarded
5. Management support and resources are essential
6. Knowledge initiatives should begin with a pilot program
7. Quantitative and qualitative measurements are needed to evaluate the initiative
8. Knowledge is creative and should be encouraged to develop in unexpected ways.
E-COMMERCE
Electronic Commerce- Penggunaan Komputer dan jaringan di dalam bisnis, dengan kata lain Jual beli produk menggunakan internet.
Ada dua jenis e-commerce, yaitu:
· Business to Cunsumer (B2C) - transaksi yg terjadi antara pebisnis dan konsumenya
· Business to Business (B2B) – transaksi yg terjadi antara dua pebisnis
BARCODE
Barcode adalah salah satu metode didalam pengumpulan dan identifikasi data secara otomatis Ditemukan dan dipatenkan senilai 2.612.994 USD pada Oktober 1952 oleh Joseph Woodland dan Bernard Silver
DEFINISI – Suatu gambar kecil yang memuat garis dan spasi sebagai kartu identitas untuk mengidentifikasi suatu produk tertentu, orang dan lokasi. Kode yang memperlihatkan batang/garis vertikal dan spasi yg mewakili simbol dan nomor tertentu
Barcode biasanya terdiri dari 5 bagian, yaitu:
1. Quite zone
2. Start character
3. Data characters
4. Stop characters
5. Another quite zone

tapi bagaimana barcode bekerja??
Scanner membaca Bar dan spasi yang ada di label. Angka hanya untuk manusia. Informasi dari scanner ditransfer ke komputer yang sudah terkodifikasi dan memuat data harga, sisa barang yg tersedia dan data lainnya
Manfaat Barcode??
Bagi Perusahaan• menunjukkan harga yang akurat,
• memperkecil kesalahan penghitungan oleh manusia, mengetahui dengan tepat persediaan barang yg ada (inventory control)
Bagi Pelanggan
• mendapatkan barang yang dicari / tidak kehabisan barang yang dicari
karena sistem akan segera memesan barang yang kehabisan stock.
• Terhindar dari kerugian, karena kemungkinan error
atau salah memasukkan jumlah uang yang harus dibayar
SYSTEM ANALYST
Suatu pekerjaan yang sangat berkaitan dengan penggunaan komputer (hardware&software). Memberikan solusi IT terhadap efisiensi dan produktifitas perusahaan
How do they Work??
BUSINESS PROCESS
Business process atau metode bisnis adalah kumpulan dari tugas-tugas yang terkait, yang digunakan untuk memecahkan permasalahan-permasalahan yang ada
Business Process haruslah:
1. Mempunyai target
2. Mempunyai input yg jelas
3. Mempunyai output yg jelas
4. Ada sumber daya
5. Ada beberapa aktifitas
6. Bisa saja melibatkan lebih dari satu unit kerja
7. Menciptakan nilai bagi customer baik internal maupun external
Bagi Perusahaan• menunjukkan harga yang akurat,
• memperkecil kesalahan penghitungan oleh manusia, mengetahui dengan tepat persediaan barang yg ada (inventory control)
Bagi Pelanggan
• mendapatkan barang yang dicari / tidak kehabisan barang yang dicari
karena sistem akan segera memesan barang yang kehabisan stock.
• Terhindar dari kerugian, karena kemungkinan error
atau salah memasukkan jumlah uang yang harus dibayar
SYSTEM ANALYST
Suatu pekerjaan yang sangat berkaitan dengan penggunaan komputer (hardware&software). Memberikan solusi IT terhadap efisiensi dan produktifitas perusahaan
How do they Work??
BUSINESS PROCESS
Business process atau metode bisnis adalah kumpulan dari tugas-tugas yang terkait, yang digunakan untuk memecahkan permasalahan-permasalahan yang ada
Business Process haruslah:
1. Mempunyai target
2. Mempunyai input yg jelas
3. Mempunyai output yg jelas
4. Ada sumber daya
5. Ada beberapa aktifitas
6. Bisa saja melibatkan lebih dari satu unit kerja
7. Menciptakan nilai bagi customer baik internal maupun external


